Introduction:
Efficient networking solutions are vital for seamless communication between services and resources in cloud environments. Amazon Web Services (AWS) offers AWS Transit Gateway, a scalable and centralized solution for connecting multiple Virtual Private Clouds (VPCs) and on-premises networks. In this article, we'll explore how to set up and utilize AWS Transit Gateway (TGW) to establish connectivity between multiple VPCs within the same region, eliminating the time-consuming process of manually accepting peering connections.
We'll understand this in 5 steps.
Step 1:Provisioning VPCs
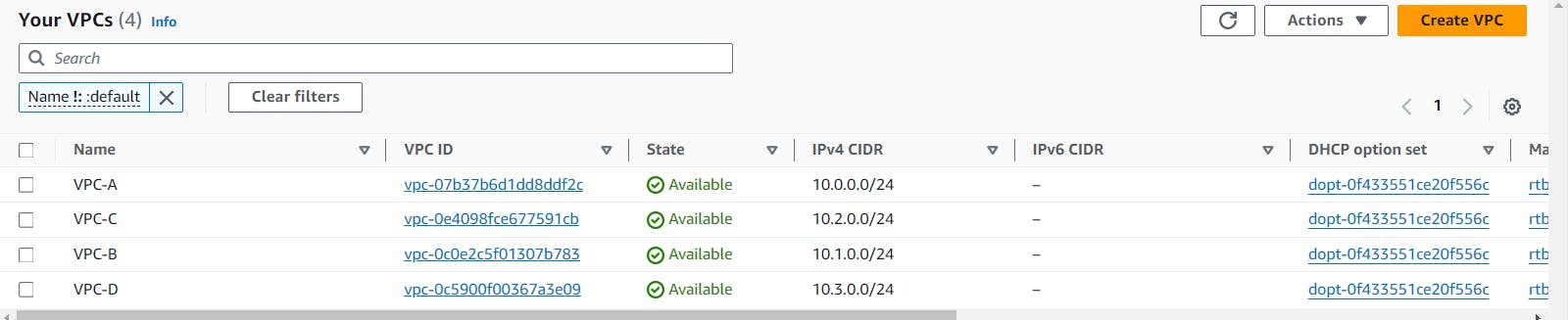
Begin by creating four VPCs within any region. For this lab, I've selected Singapore region. Ensure that each VPC has a unique CIDR block assigned to it, and also allocate a common CIDR block to all the VPCs. This setup ensures that there is no overlapping CIDR and allows for seamless communication within the VPCs.
CIDRs for each VPC:
VPC-A - 10.0.0.0/24
VPC-B - 10.1.0.0/24
VPC-C - 10.2.0.0/24
VPC-D - 10.3.0.0/24
Common CIDR - 10.0.0.0/8
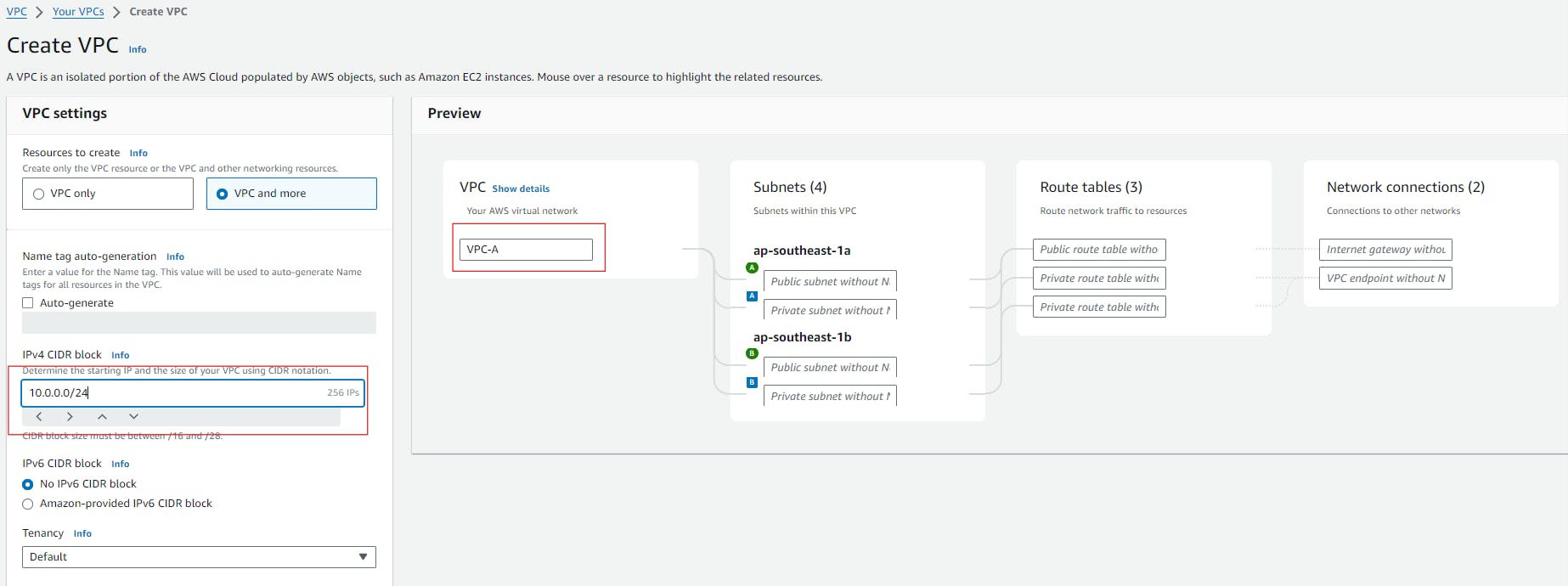
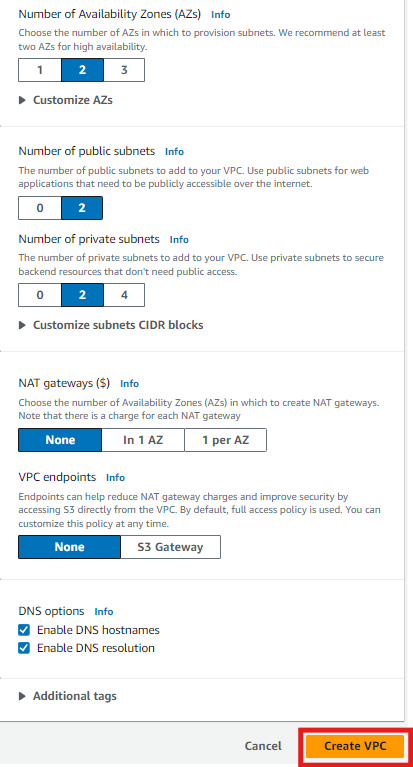
Select None for VPC endpoints, keep the other settings as it is and Click on Create VPC. It create our first VPC (VPC-A). Similarly create the other 3 VPCs (VPC-B, VPC-C and VPC-D).
Step 2: Setting up AWS Transit Gateway
Next, create an AWS Transit Gateway in the Singapore region. Provide a name and description for the Transit Gateway, and leave all other options as default. This Transit Gateway will serve as the central hub for routing traffic between the VPCs.
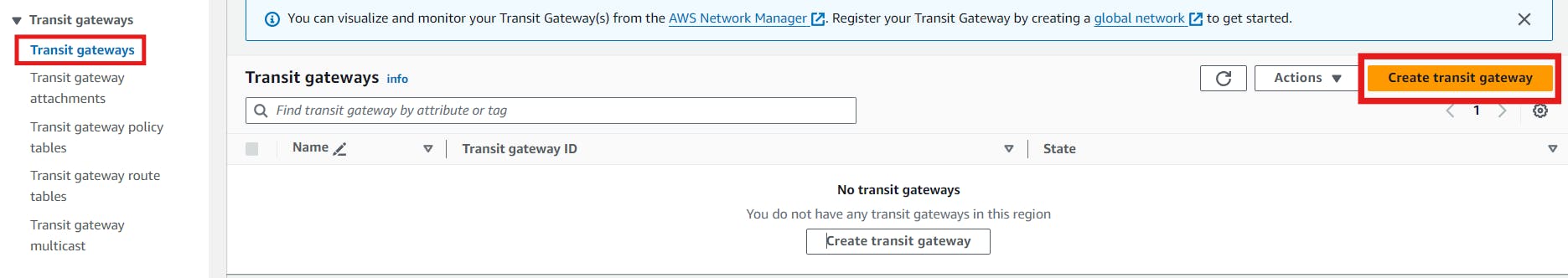
I named it as MyTGW and the same is given as Description. Keep the default settings and click on Create.
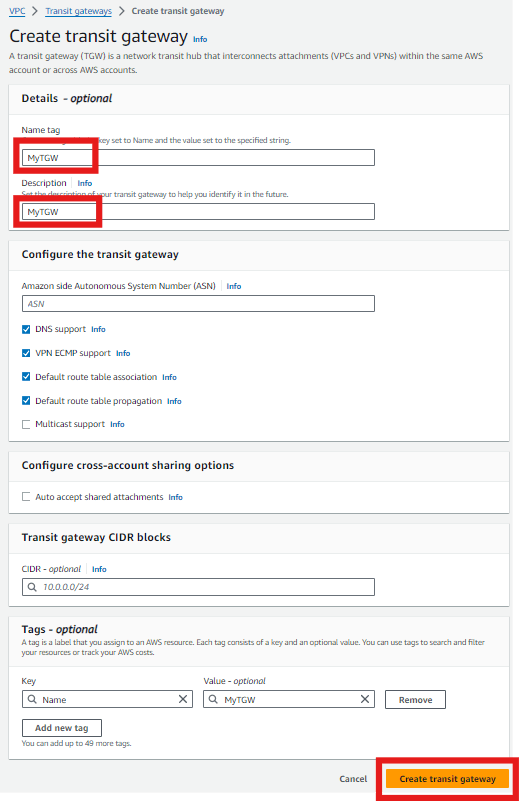
This will take some time to create the TGW.
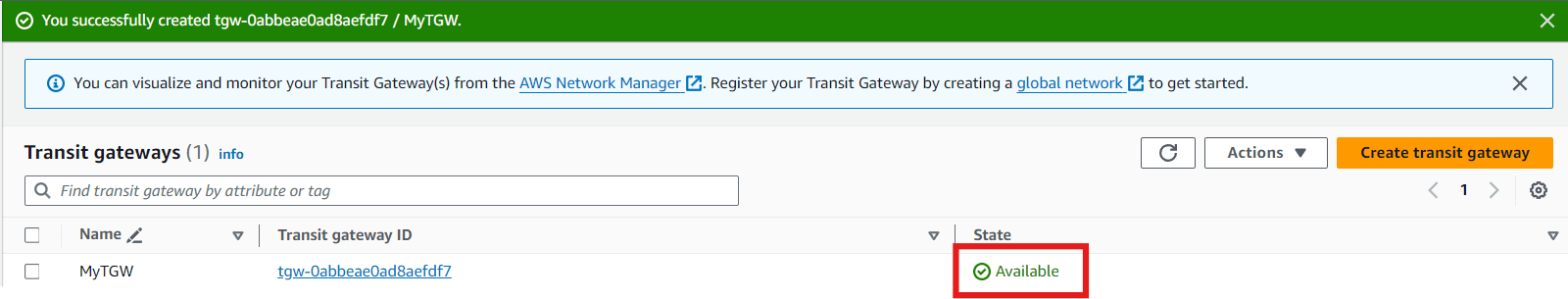
The state is changed to Available. Now we'll go to transit gateway attachments and create attachments.
Step 3: Creating Transit Gateway Attachments
Once the TGW is set up, create TGW attachments for each VPC. Specify the TGW ID and choose the attachment type as "VPC." Select the respective VPC and subnets for each attachment. This establishes the connectivity between the TGW and the VPCs.
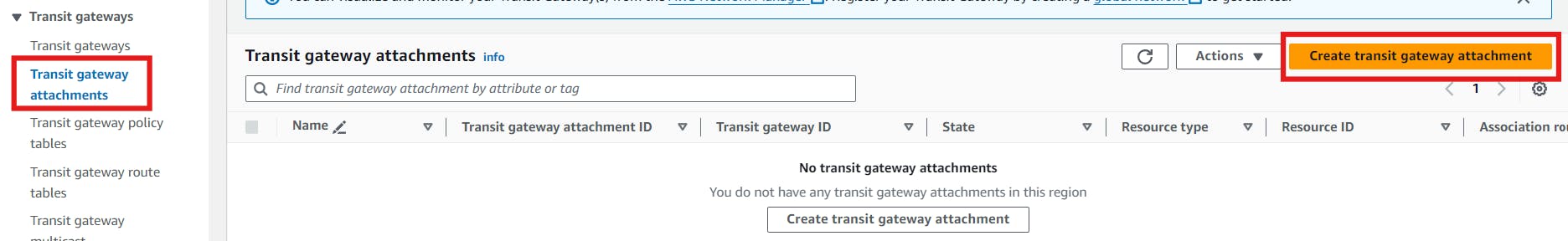
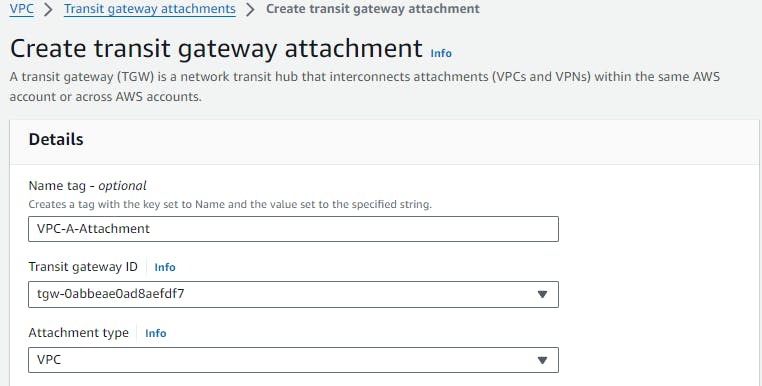
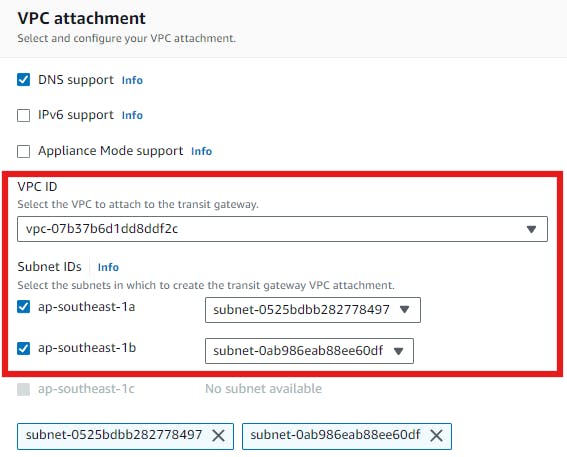
We've to do this step carefully. I chose VPC-A. For this, we need to select the 2 subnets of explicit association. In my case one subnet is ending with 497 and another with 0df.
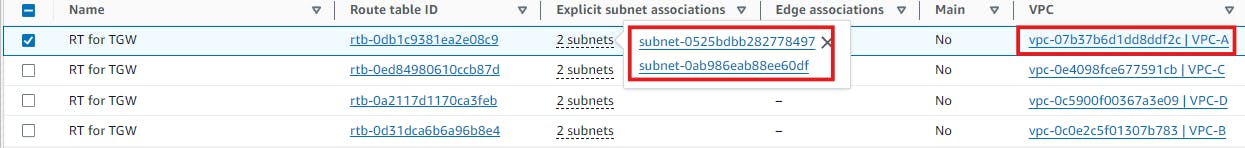
Similarly do association for the other VPCs.
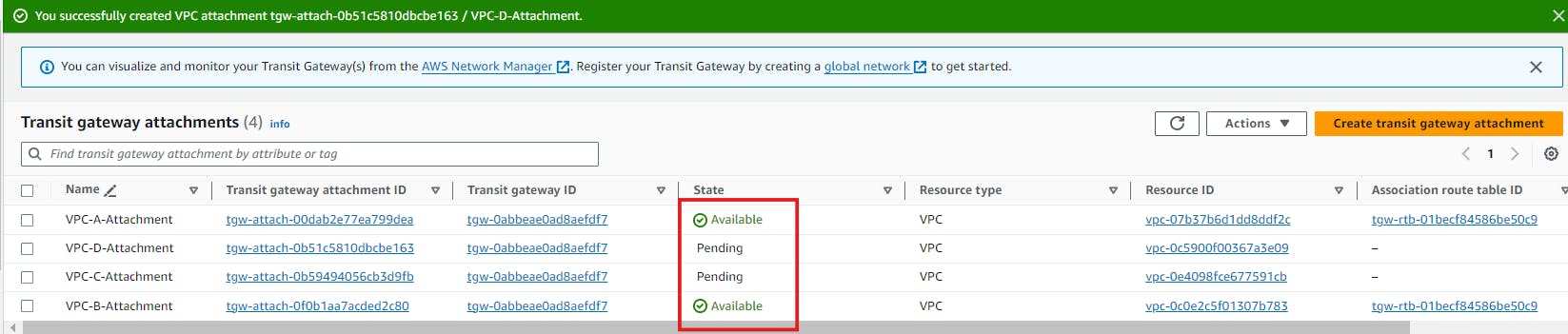
Wait until the state for all the attachments is changed to Available. Meanwhile, configure the route entries.
Step 4: Configuring Route Entries
Now, configure route entries in the route tables associated with the VPC subnets. Add a route entry for the common CIDR block (10.0.0.0/8) with the TGW as the target. This ensures that traffic destined for the common CIDR block is routed through the TGW.
We'll now go to Route Tables, and select those Route Tables where there are 2 explicit subnet associations are present as shown below.
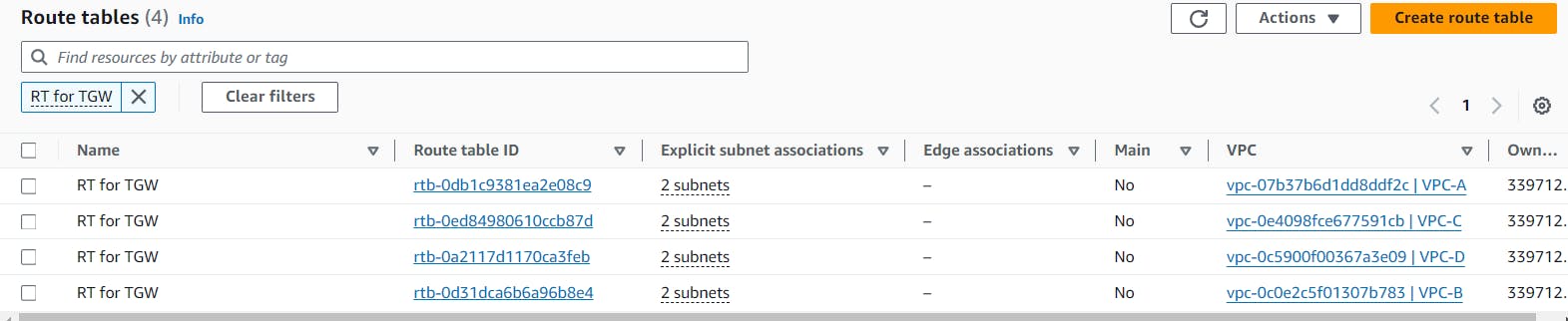
I've renamed them as RT for TGW. For each of this RT, we've to add a route to the TGW to route the traffic.
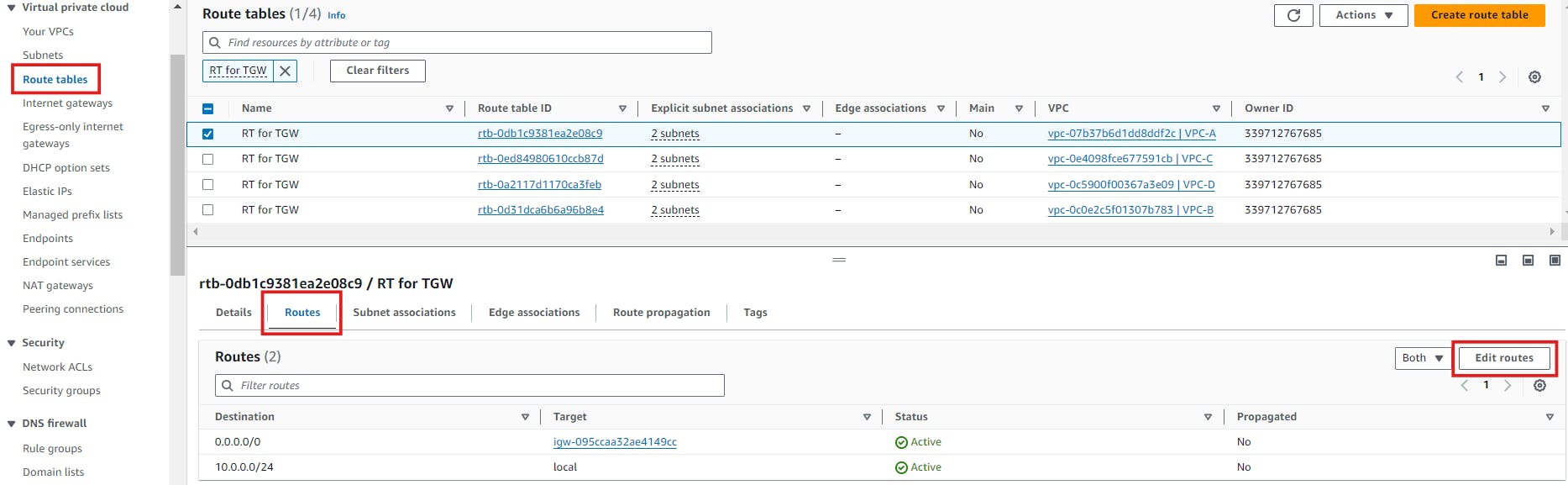
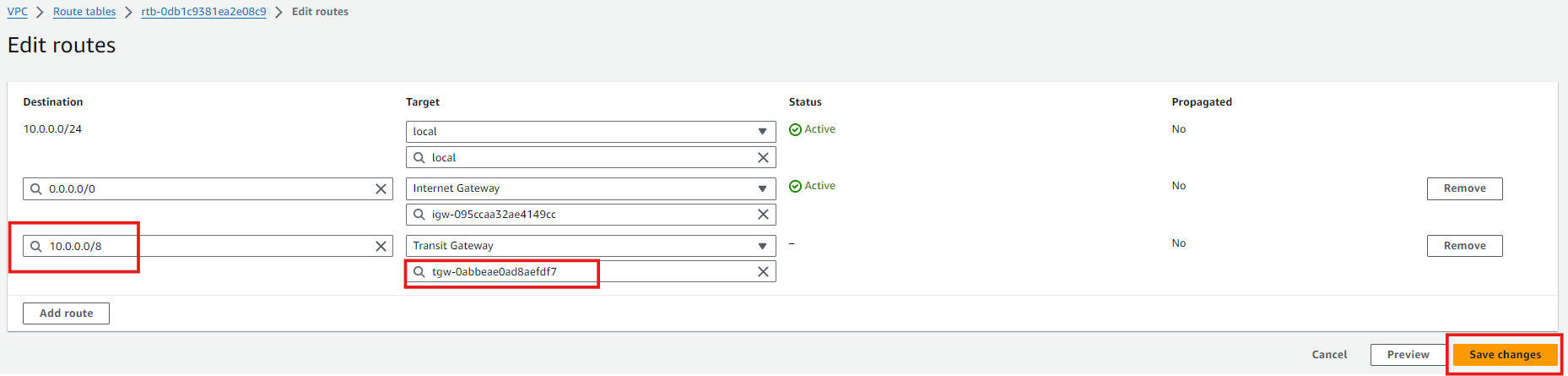
Click on Add route -> Enter the common CIDR in the destination field, select the transit gateway and save it.
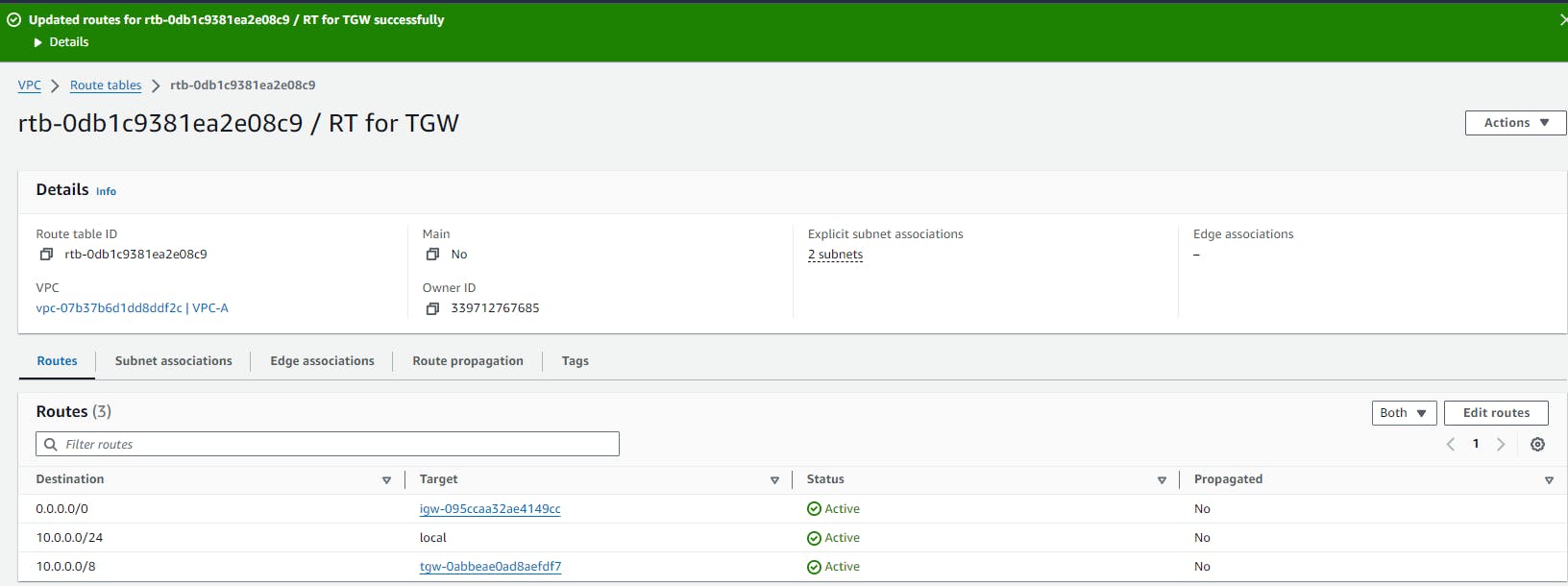
Route is added. Similarly, repeat this process for the remaining 3 RTs.
Step 5: Testing Connectivity
To test the setup, launch EC2 instances in two different VPCs. Ensure that the instances are launched in subnets associated with the route tables containing the Transit Gateway route entry. Attempt to communicate between the EC2 instances using their private IP addresses. For this test purpose, I'll create a Windows EC2 instance in VPC-A and an Amazon Linux EC2 in VPC-D. Let's test this.
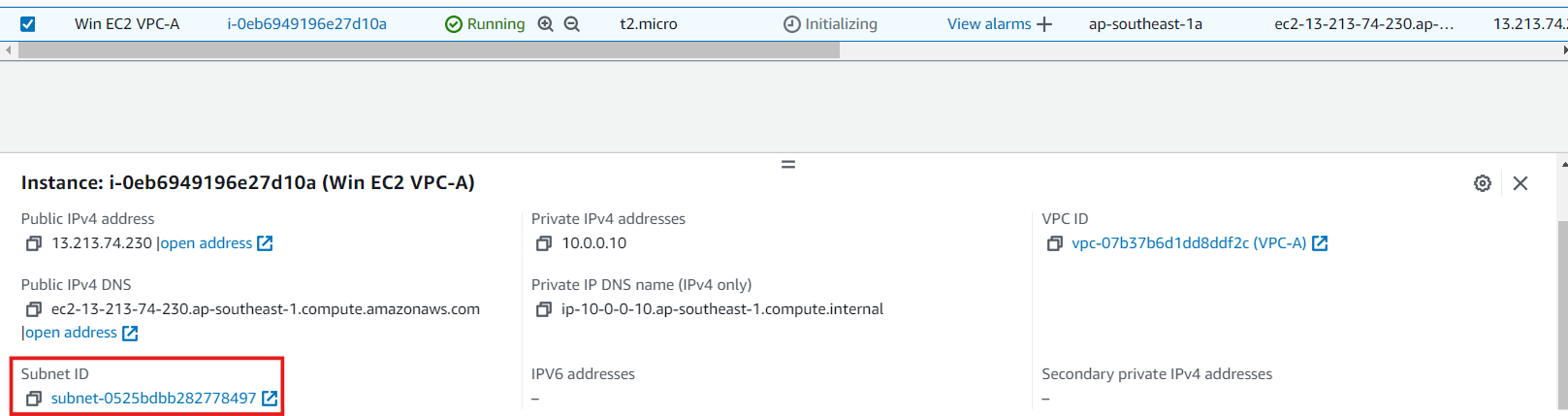
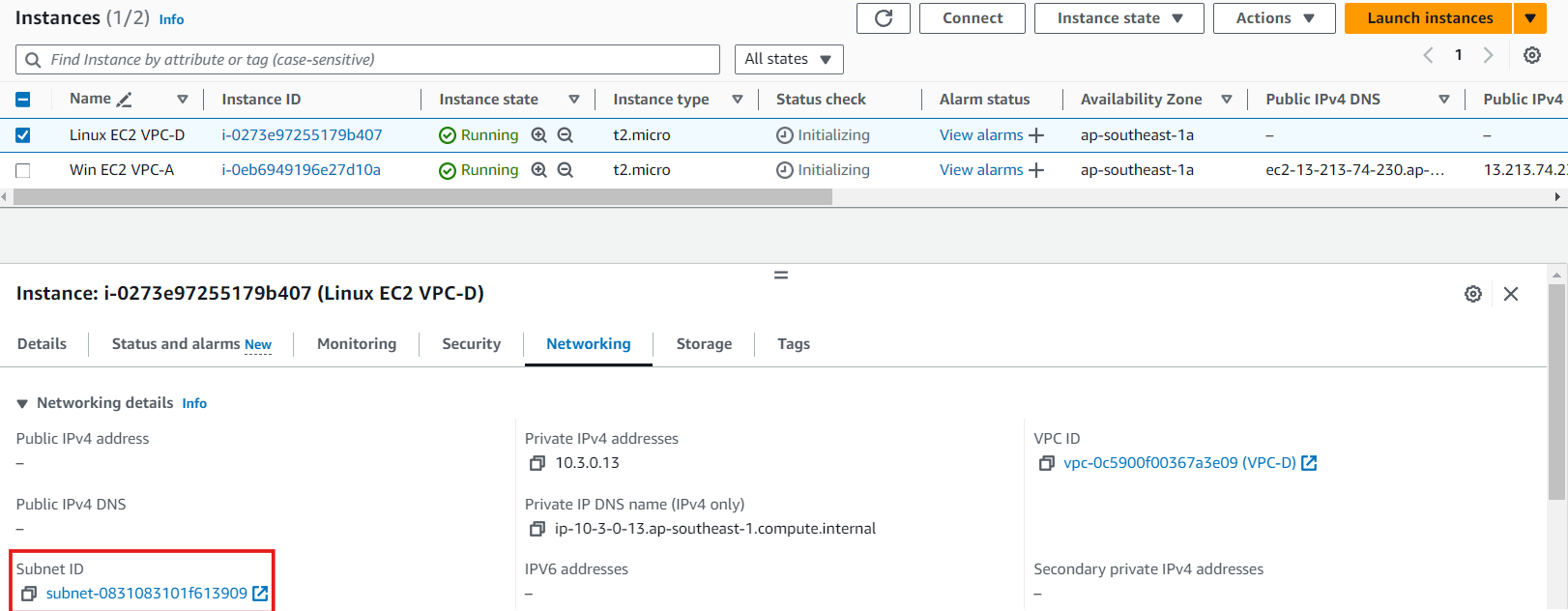
First let's connect to Windows EC2 using RDP. From Windows, we'll connect to Linux via SSH using MobaXterm.
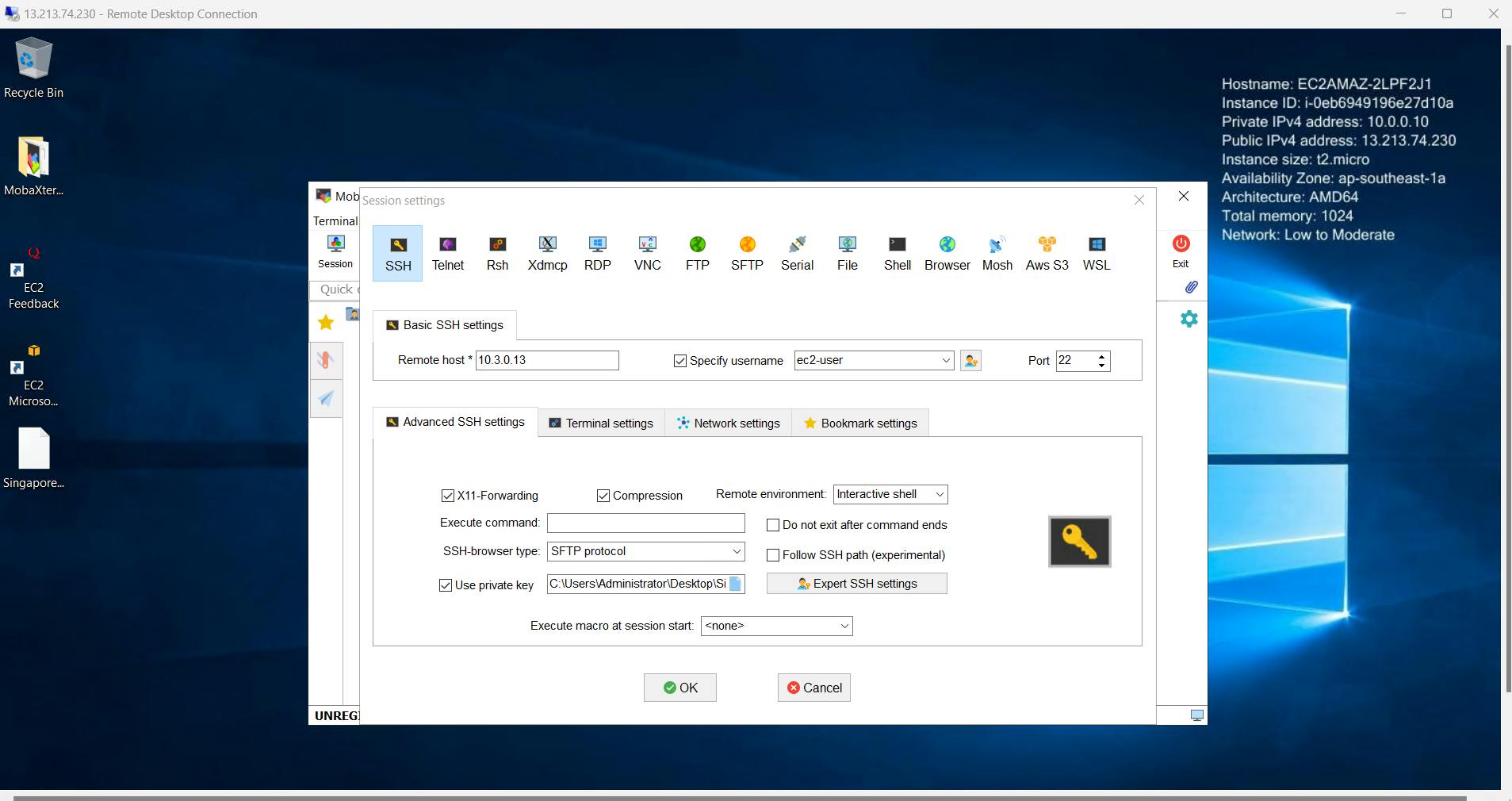
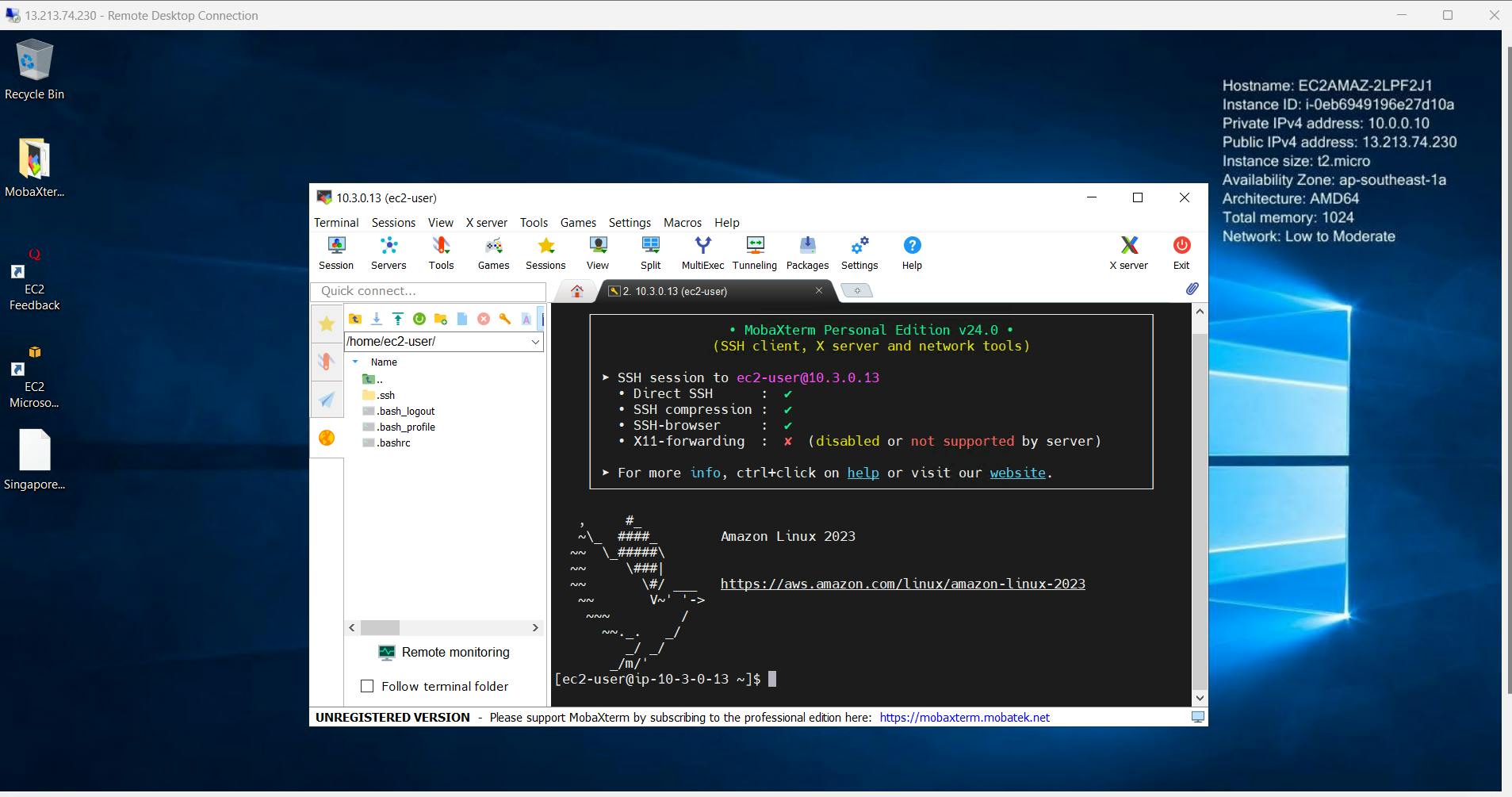
Successful communication indicates that the Transit Gateway is functioning correctly.
This communication is no longer possible, If we delete the TGW.
Step 6: Cleanup
After testing, clean up the resources in the following order
1. Delete the Transit Gateway attachments,
2. Delete the Transit Gateway, and
3. Delete the routes explicitly added in the RTs.
Verify that connectivity is disrupted after cleanup, ensuring that resources are no longer accessible across VPCs. Finally, Terminate the EC2 instances.
Conclusion:
AWS Transit Gateway offers a scalable and efficient solution for interconnecting multiple VPCs within the same region. By following the steps outlined in this article, users can establish a robust network architecture that enables seamless communication between VPCs while maintaining security and scalability. Embracing AWS Transit Gateway empowers organizations to streamline their networking infrastructure and drive innovation in the cloud computing space.